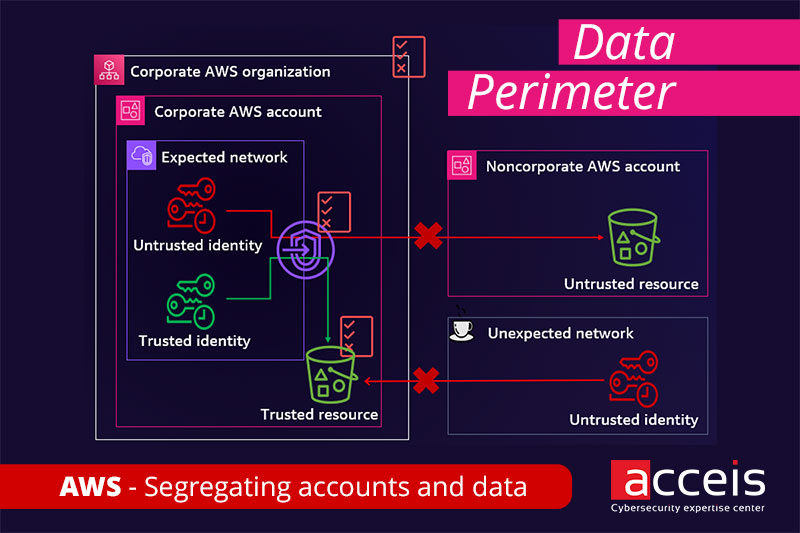
par Alexandre RIPOTEAU | Juin 18, 2025 | Articles techniques EN
In large AWS environments, resources and users are sometimes segmented into units within an organization. This allows access and usage to be segregated. However, it is difficult to effectively control all resources at the organizational level. Data perimeter allows...

par Tristan D'audibert | Août 28, 2024 | Articles techniques EN, Développement, Outils et méthodes
This article is a tutorial on how to create an eBPF program using a tracepoint. If you are not familiar with eBPF, please refer to our introduction to eBPF, or to the official documentation. To follow this article in the best conditions, we recommend you read part 1...

par Alexandre Zanni | Juil 18, 2024 | Articles techniques EN, Non classifié(e)
This article will look at various techniques for breaking SSH private keys. An unencrypted private key can be used by anyone with access to the file. An encrypted key, on the other hand, can only be used by those who know the password needed to decrypt the key. Thus,...

par Alexandre RIPOTEAU | Juil 5, 2024 | Articles techniques EN, Non classifié(e)
In order to prevent CSRF (Cross-Site Request Forgery) attacks, security best practices such as those of OWASP recommend the use of a synchronization token model or anti-CSRF token. The absence of a token does not necessarily lead to vulnerability, and several factors...

par Arthur DELOFFRE | Mai 15, 2024 | Actualité EN, Articles techniques EN, Non classifié(e)
Insomni’hack is a cybersecurity conference founded and organized by SCRT S.A. (now Orange Cyberdefense Switzerland) since 2008. It takes place in Switzerland, and lasts a week for each edition. This year, it took place from April 22 to 26, 2024 at the SwissTech...

par Tristan D'audibert | Fév 7, 2024 | Articles techniques EN, Développement, Outils et méthodes
This article is a tutorial on how to create an eBPF program using a tracepoint. If you’re not familiar with eBPF, you can refer to our introduction to eBPF, or to the official documentation What is a tracepoint? How do I create one with eBPF? What are the steps...

par Tristan D'audibert | Jan 30, 2024 | Articles techniques EN, Développement, Outils et méthodes
Are you familiar with eBPF ? Do you know its purpose or how it works ? Today, I’m trying to outline a brief overview of what, for me, is a revolutionary and very promising technology for the future of computing. eBPF is a revolutionary technology with origins in...

par Alexandre Zanni | Jan 25, 2024 | Articles techniques EN
Introduction Varonis Threat Labs has discovered a new Outlook vulnerability (CVE-2023-35636) among three new ways to access NTLM v2 hash codes by exploiting Outlook, Windows Performance Analyzer (WPA) and Windows File Explorer. With access to these hash codes,...

par Alexandre Zanni | Jan 8, 2024 | Actualité, Articles techniques EN, Outils et méthodes
In this article, we’ll demystify the nuts and bolts of PXE boot, and explain how to retrieve and analyze a PXE image to find secrets (such as an AD domain account). Note: This article is also available in french 🇫🇷. What is PXE? 🔍 In...
par Alexandre Zanni | Nov 30, 2023 | Articles techniques EN, Outils et méthodes
This article describes the methodology for Active Directory domain accounts takeover through LDAP pass back attack on printers. Note: This article is also available in french 🇫🇷. Goal 🥅 In the context of an internal infrastructure penetration...
par Alexandre RIPOTEAU | Sep 29, 2023 | Articles techniques EN, Outils et méthodes
Visual Studio Code is, according to a Stack Overflow survey, the most popular IDE, and has been the subject of security research and possible compromise. This article succinctly details the research done by others on this IDE, presents the IDE’s trust model, and...
par Alexandre Zanni | Sep 6, 2023 | Articles techniques EN
Note: This article is also available in french 🇫🇷. Introduction Kirby is a Nitendo video game character open-source PHP CMS oriented for creators and designers. The vulnerability presented in this article is an XML External Entity (XXE) in...
par Alexandre Zanni | Sep 4, 2023 | Articles techniques EN, Challenges
The vulnerability to be detected for this challenge was a local file disclosure due to incorrect path limitation. Solving the challenge doesn’t require any special knowledge, just reading the Actix web framework documentation to understand how the methods...
par Alexandre Zanni | Juil 24, 2023 | Articles techniques EN, Challenges
The vulnerability to be detected for this challenge was a resource (variable) injection that enabled authentication to be bypassed. Solving the challenge requires knowledge of certain PHP functions. Note: This article is also available in french 🇫🇷....
par Alexandre Zanni | Juin 26, 2023 | Articles techniques EN, Challenges
The vulnerability to detect for this challenge was an SSRF exploitable with a workaround using a DNS rebinding (TOCTOU). The challenge resolution does not necessarily require knowledge of the language (Ruby) or the web framework (Roda). Indeed, the problem being...










