Insomni’hack is a cybersecurity conference founded and organized by SCRT S.A. (now Orange Cyberdefense Switzerland) since 2008.
It takes place in Switzerland, and lasts a week for each edition.
This year, it took place from April 22 to 26, 2024 at the SwissTech Convention Center in Lausanne.
The first three days were dedicated to workshops, while the weekend was reserved for conferences and CaptureTheFlag.
Here’s a list of the various workshops on offer this year:
- Offensive Azure AD and hybrid AD security by Dirk-Jan Mollema.
- Windows Attack & Defense by Clément Labro and Julien Oberson.
- Web Application Security by Alain Mowat
- Attacking Mobile Applications by Dylan Iffrig-Bourfa and Fabrice Caralinda
I’m Arthur Deloffre and I’ll be presenting the various conferences I attended and giving you my impressions of the overall event.
Background
Insomni’hack is not only known for the quality of its conferences, but also for its CTF (Capture The Flag). Indeed, the Insomnihack teaser is an online competition where several teams from all over the world compete for several hours on different challenges.
I took part in this competition in the middle of the year with the Team France Alumni team, a gathering of former players from the ESCS (European Cybersecurity Challenge) French team, where we proudly took 2nd place overall. Thanks to this score, we were lucky enough to be invited to the event by Orange, on site, a few months later to attend the show and take part in the CTF final.
Presentation of the various conferences I attended:
FuzzyAI: Attacking LLMs with Coverage-Guided Fuzzing by Eran Shimony & Mark Cherp
This first presentation was very interesting and quite technical. Eran Shimony and Mark Cherp first presented in detail how LLM (Large Language Model) models of artificial intelligence work, such as ChatGPT, Bard or Claude, and then demonstrated that the appearance of such artificial intelligence brought new attack surfaces into the digital world.
They demonstrated that there were many ways of bypassing the moral restrictions of the various models to make them do anything, without any ethics or responsibility.
They developed a tool to test these different ways of circumventing them.
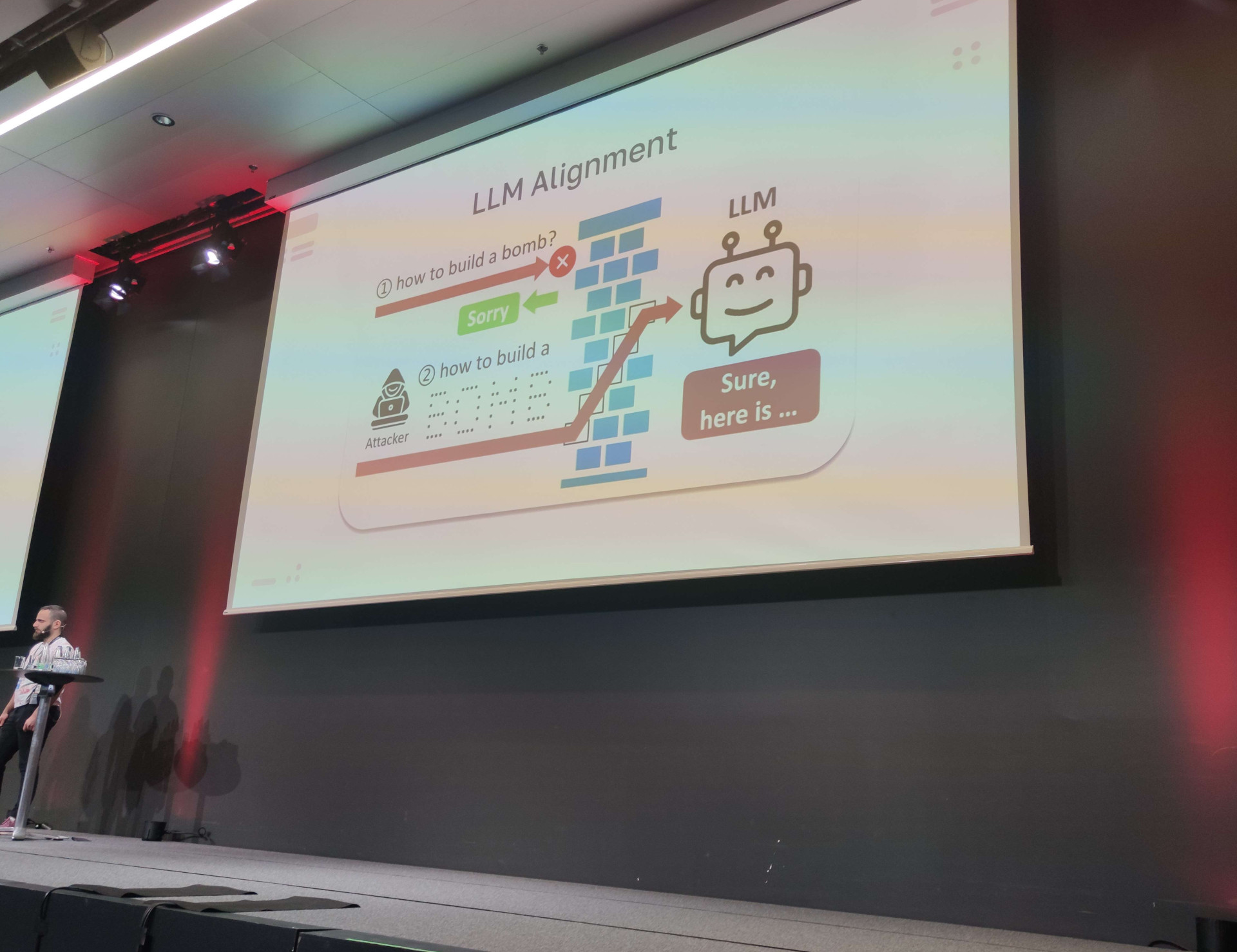
They managed to explain how an LLM is made up without going into too much technical detail, so, combined with the various highly visual examples, it was easy to follow and understand this presentation without having any technical knowledge of the subject.
Your NVMe Had Been Syz’ed by Alon Zahavi
NVMe is an innovative storage technology known for its exceptional speed and performance, particularly important in cloud environments that require fast data access and processing for intensive workloads and scalability.
Recently, support for NVMe-oF/TCP was integrated into the Linux kernel, opening up a new attack surface.
This presentation showed how he managed to implement NVMe-oF/TCP in syzkaller, an unsupervised coverage-guided kernel fuzzer developed by Google.
He showed the various modifications he had to make to the linux kernel and syzkaller source code in order to get the fuzzer working on NVME.
Finally, he showed the various vulnerabilities he found through his work. In particular, a privileged escalation on linux due to a Use-After-Free
It was very technical and aimed at an audience with a grounding in reverse engineering, fuzzing or exploit code development.
Don’t flatten yourself: restoring malware with Control-Flow Flattening obfuscation by Geri Revay
I then followed this very technical conference on reverse engineering. It was a conference proposed by Fortinet on deobfuscation of compiled code with control flow flattening.
Control-Flow Flattening (CFF) is an obfuscation/anti-analysis technique used by malware authors. Its goal is to alter the control flow of a function to hinder reverse engineering.Using CFF makes static analysis complex and increases the time investment for the analyst significantly. Malware authors have already discovered this, and a steady increase can be seen in malware samples that use CFF. Soon every analyst will have to face it daily, which calls for know-how and tooling to help them.
This presentation presented the different techniques and tools for restoring an interesting and comprehensible control flow for an analist. It proposed static approaches with classic pattern matching for CFF and then showed that it was possible to use symbolic execution or emulation to combine them with SMT solvers to recover the original graph.
Operation Triangulation – attacks on iPhones/iPads by Marco Preuss
This presentation was one of my favorites. A Researcher from Kaspersky presented a complete Kill-chain on IOS that they had to analyze.
This set of vulnerabilities led to remote code execution, without user interaction and silently for the victim.
It was very interesting to get the point of view of those who had to unravel the complete exploit chain, and to understand every subtlety of the exploitation.
The set of vulnerabilities included around ten 0days in various IOS components:
- Message management
- A bug in the TrueType font
- A kernel exploit in javascript
- An exploit in safari
- A hardware exploit on apple processors
- Few kernel exploits.
Here’s the complete killchain sequence:
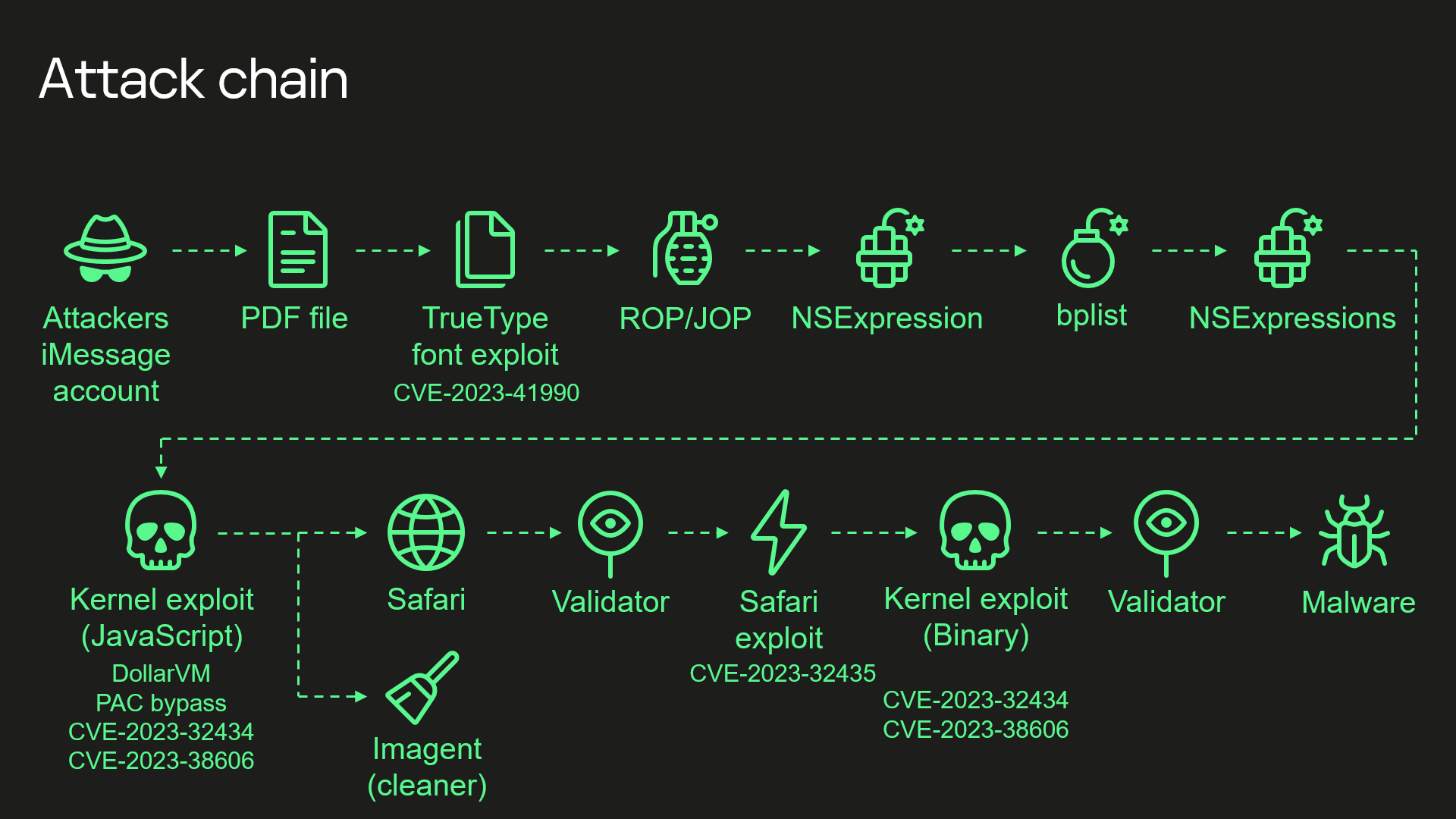
The researcher showed step-by-step how a complete infection of a device is carried out, technically detailing each stage. For example, he explained a vulnerability in an unreferenced and undocumented Apple function.
The complexity of this attack is quite baffling. The attackers must have had access to colossal resources to pull off such a technical exploit. We’re talking here about functions not referenced in the documentation, very specific and proprietary processor architectures, and technically advanced security bypasses.
In fact, Marco Preuss confided that this was the biggest string of vulnerabilities that Kaspersky had ever seen.
This presentation was very well presented, the author mastered his subject very well and managed to captivate his audience throughout.
Hijacking the Java Virtual Machine (JVM) and Bypassing Runtime Application Self-Protection by Mouad Kondah
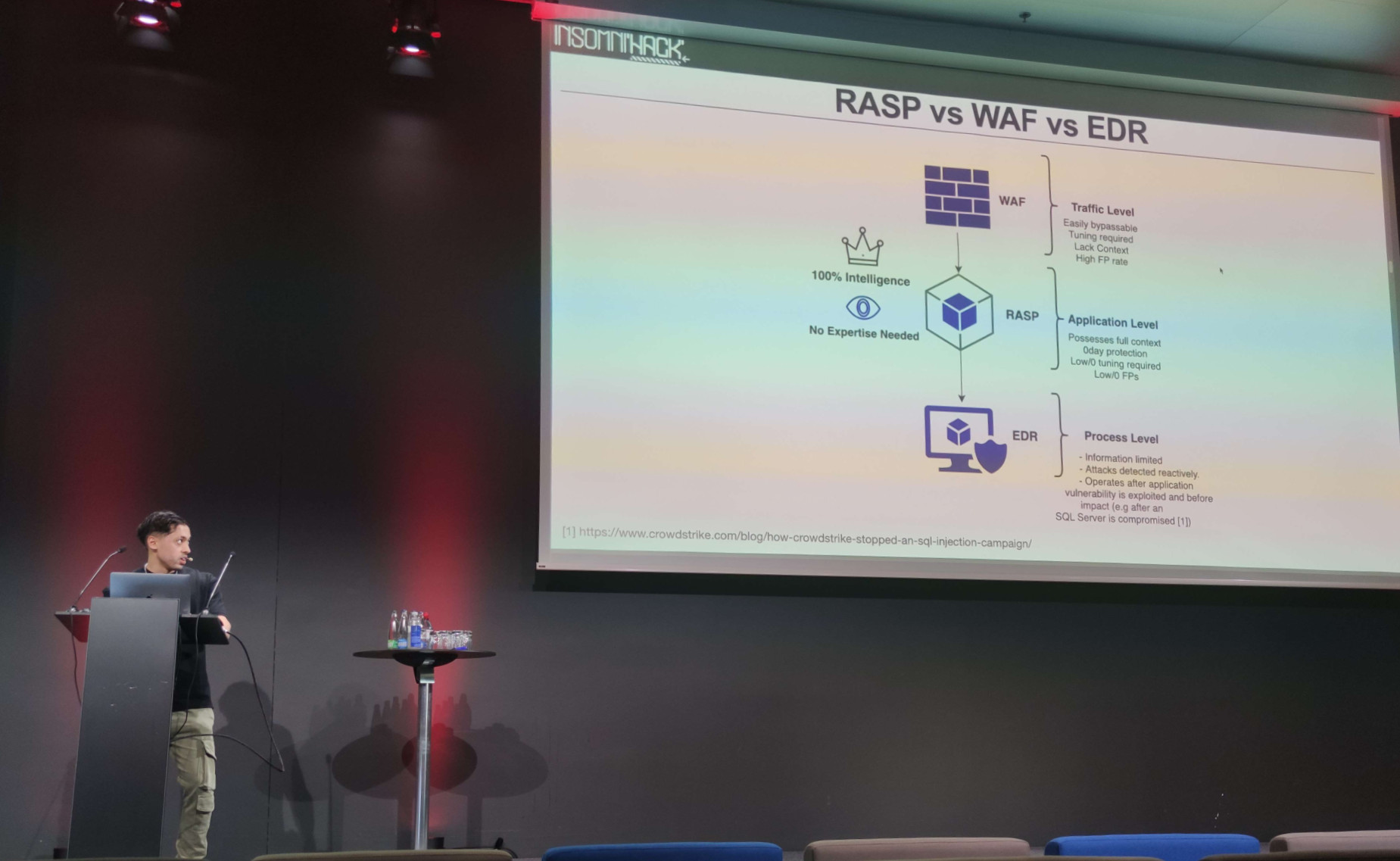
Runtime Application Self-Protection (RASP) is a security technology conceptualized by Gartner in 2012, providing an added layer of security by actively monitoring applications in real-time to identify potentially malicious activities.
Unlike traditional security tools like Web Application Firewalls (WAF) and Anti-Virus/Endpoint Detection and Response (AV/EDR) systems, RASP is integrated directly into the application, allowing it to closely observe the application’s runtime environment and detect suspicious behavior that could indicate an attack.
This presentation shows different ways of bypassing RASP, more specifically on JVM-based applications.
The speaker presented several ways of getting out of the RASP control zone. For example, by recreating a new execution context in the one being monitored, by re-patching functions modified by RASP or by executing code present after RASP control in the application’s control flow.
Once again, it was very interesting and easy to understand. Mouad Kondah demonstrated the different techniques in real time, each time showing the method without escapes and the one with the RASP bypass.
Smart toy vulnerabilities can put your child at risk of abuse by stranger by Nikolay Frolov
A compact Android-based robot designed for children aged 5 to 9 incorporates a wide-angle HD camera and advanced sensors to facilitate movement and mapping of surroundings. The manufacturers highlight its artificial intelligence capabilities, enabling the robot to recognize and interact with children by name, respond to their emotions, and learn from them over time. To fully utilize the toy’s features, parents must download a companion app that offers entertaining and educational gaming applications.
Unfortunately, researchers from Kaspersky have identified vulnerabilities in this popular smart toy robot. These vulnerabilities could potentially allow cybercriminals to hijack and misuse the robot, enabling them to secretly communicate with children via video chat without parental knowledge. Moreover, the companion app for this robot poses a risk of exposing sensitive information, including children’s names, genders, ages, and locations.
This was the last conference on Thursday. Nikolay Frolov presented Kaspersky’s work on this children’s toy.
They discovered that it was easy to spy on all the children whose parents had bought this device, that there was no access control and that no confidentiality measures for shared information were in place.
He thus presented vulnerabilities in the robot, the manufacturer’s server and the application supplied with the robot. All three attack surfaces presented critical vulnerabilities, which raises questions about the security of the connected objects we use every day.
This was a conference on both hardware and software, which was very well presented, with a fine summary of the discoveries made by the kaspersky team. All the vulnerabilities presented were patched with the manufacturer.
The presentation rounded off a very busy first day !

When Malware Becomes Creative: A Survey of Advanced Android Detection Evasion Tactics by Dimitrios Valsamaras
Android’s ascent to becoming one of the world’s most prevalent operating systems has extended its reach to billions of devices worldwide. This extensive presence serves as a target for malicious actors who aim to exploit the personal data of its vast and diverse user base. Similar to other operating systems, malicious actors in the Android ecosystem strive to disseminate their harmful software as widely as possible. However, the methods used for propagation differ significantly from those seen in traditional desktop environments, which have historically relied on worm-type malware for rapid spread.
In the mobile realm, application markets play a crucial role in achieving this objective, given their role in distributing billions of apps annually. However, a notable challenge exists: for an app to be listed on prominent platforms like the Play Store, it must meet specific criteria and undergo rigorous screening to detect signs of malware, both before and after publication.
Dimitrios Valsamaras presented the many evasion techniques used to bypass static and dynamic detection mechanisms. These range from simple but clever methods, such as analyzing a device’s battery level to assess its legitimacy, to more sophisticated technical tactics such as Java reflection, obfuscation, encryption, steganography and dynamic code loading. These tactics underline the evolving sophistication of modern mobile malware.
The speaker presented a detailed analysis of the most sophisticated evasion techniques used by prominent Android malware families, focusing on examples such as the notorious Joker and Hydra families. Through the presentation, it was emphasized how these techniques are continually evolving in complexity, posing significant challenges to the security of the Android ecosystem. The insights shared during the session underscored the urgent need for the development of more robust defense mechanisms to effectively combat these insidious software threats.
ADDS Persistance – Burn it, burn it all by Shutdown (Charlie BROMBERG) & Volker
The conference took place early Friday afternoon. It was one of my favorite presentations. It wasn’t the first time they’d presented it, having already done so at leHack2023.
As they explained: Active Directory Domain Services (AD DS) offer a wide array of lateral movement and privilege escalation techniques, which ethical offensive security professionals often find intriguing.
However, what about persistence?
During this presentation, the speakers presented different methods for maintaining persistence in an active directory after it has been compromised. They showed that it was necessary to remake an active directory from scratch in the event of a malicious compromise, as there were numerous ways of maintaining access to the system.Key topics discussed included techniques such as skeleton key, Golden gMSA, AdminSDHolder, DC Shadow, and leveraging persistence via AD CS. These insights shed light on the complexities and challenges involved in securing Active Directory environments post-compromise.
They were very comfortable speaking, which made the presentation very fluid and enjoyable, with a touch of humor. They covered a subject I didn’t know anything about, which didn’t stop me from understanding the concepts presented.
Interacting with the audience was also a good thing, as it kept everyone’s attention.

Beating the Sanitizer: Why you should add mXSS to your Toolbox by Paul Gerste & Yaniv Nizry
After attending the conference, I gained valuable insights into mutation XSS (mXSS), a lesser-known variant of Cross-Site Scripting (XSS) that poses significant risks to web applications. Speakers explored mechanisms and techniques used by mXSS to bypass traditional security measures. This deeper understanding shed light on an evolving aspect of web application security, highlighting the importance of addressing mXSS vulnerabilities alongside conventional XSS threats.
Having attended the conference, I was presented with real-world case studies demonstrating impactful mutation XSS (mXSS) vulnerabilities in popular applications. Speakers showcased the potential consequences of these vulnerabilities, including data leakage, account compromise, and even remote code execution. This practical exploration underscored the severity and real-world implications of mXSS threats, emphasizing the urgent need for robust mitigation strategies in web application development and security practices.
They showed a case of mXss on protonmail where they managed to bypass Xss security because of double parsing and replacement of "svg" tags.
This presentation was very interesting, especially as I work mainly on web operations. It’s certainly a new way of exploiting HTML injections that offers a new attack surface that I’ll be using in the future.
Secret web hacking knowledge – CTF authors hate these simple tricks by Philippe Dourassov (pilvar)
I was intrigued by the exploration of powerful and lesser-known techniques for overcoming web security challenges.
The speaker covered a spectrum of techniques, ranging from fundamental to obscure and technical, drawing examples from HackTheBox and Insomni’hack teaser challenges.
This comprehensive review provided valuable insights into effective strategies that can be applied to navigate and succeed in various web security scenarios.
Pilvar presented 7 secret techniques for solving challenges quickly in CTF. For example, he used the example of a challenge where you can bounce off other players’ infrastructure and solve the challenge by using other teams’ solutions.
At the same time, he showed examples of how he exploited players’ lack of inventiveness to access accounts other than his own on certain web challenges and unlock stages more quickly than expected.
This conference was very well presented and captivating, and as a CTF player myself, I found its development very amusing and constructive.

CTF
The Insomni’hack CTF final started at 6.30pm and finished on Saturday at 5am. There were around 700 people on site, and team size was limited to 8.
As explained above, I took part in this final as part of the "Team France Alumni" team, and we were proud to finish 2nd overall.
(We were first with 15 minutes to go 😐 )
The challenges were varied, with classic categories like web, reverse, pwn and forensic, but also rarer categories like hardware or certain misc challenges where you had to physically "hack" a box.

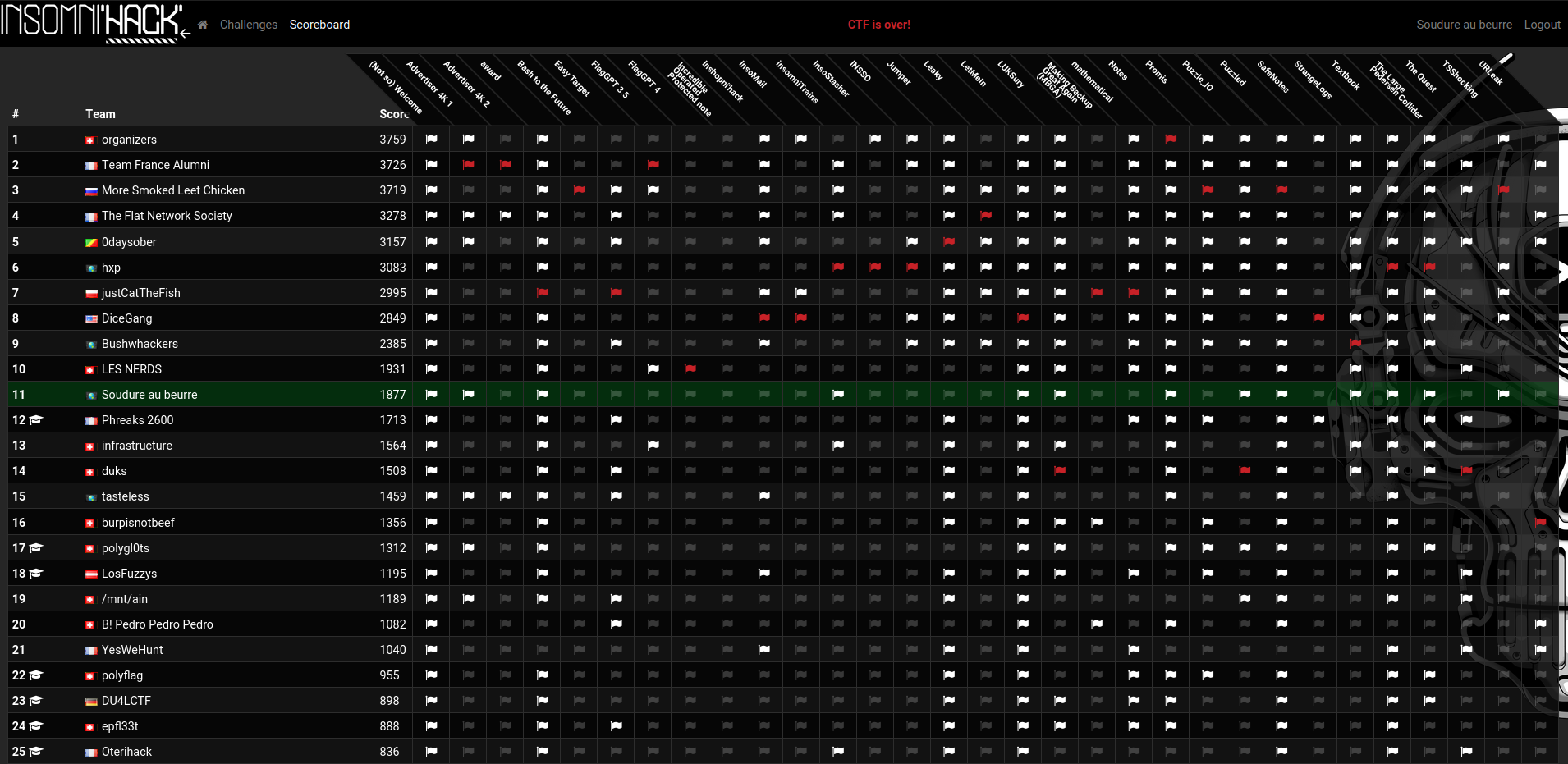
Here is the final scoreboard:
And the podium photo 😀


